ABSTRACT in my word
UAF 作为一种典型的漏洞类型;能够在其被触发的时候就被检测到是十分有意义的。本文目标就是构建一套对于编译后的二进制执行程序的检测系统。一般该类型的系统是通过对每次allocate操作的创建一个别名的映射(alias-based solution),并在其Free的时候清理相关的内存,但是由于频繁的用户态/内核态严重的影响了程序的性能;本文在传统的alias-based solution通过Kernel Mode Linux在Ring 0权限下直接操作页表结果,实现高性能的UAF检测系统。
Contributions
A new approach to detect use-after-free bugs based on alias allocation with virtualization-based direct page table access.
A novel solution for alias reclaiming.
A prototype of DangZero using KML as a privilege backend.
An evaluation to show that DangZero significantly outperforms prior detection systems and even state-of-the-art GCstyle protection systems on long-running benchmarks.
Limitation
该工具依赖Kernel-Mode-Linux完成功能扩展,因此无法在 > v4.0版本的内核上使用;【貌似Github上已经有支持4.4版本的KML patch】
DangZero目前暂未做到Thread-safe;需要引入页表锁来实现线程安全;
对于依赖系统malloc或是mmap的程序使用会有一些难度;
过强的安全隔离机制会给进程间通信带来新的挑战;
Directory
Background
2.1 Use-after-Free : 简单介绍UAF漏洞
2.2 Page Tables : 简介内核对页表的管理模式
2.3 Access to privileged CPU features
Threat Model
- 假设攻击者准备利用progam中的利用UAF漏洞来完成信息泄漏/权限提升等目标;防御利用UAF完成的内存重用或是其他的利用技巧;但不会防御其他类型的攻击(如 buffer overflow).
DANGZERO [重点关注部分]
Introducing the architecture of DangZero
4.1 Temporal safety through page protection
4.2 Creating and invalidating aliases
4.3 Alias reclaimer
IMPLEMENTATION
5.1 Privilege backend
5.2 Alias page tables
5.3 Supporting fork
5.4 Optimizing page entry lookups
EVALUATION [篇幅很长,但是对我意义不是很大,跳过了]
My Key Notes
2-2 PageTable
大多数64位架构使用 4级页表,每个页表由512个条目组成,产生48位(256TB)的虚拟地址空间。一个48位(256TB)的虚拟地址空间。
当使用硬件虚拟化扩展运行虚拟机(VM)时,有两层页表:客户页表和主机上的扩展页表(EPT)。给客户带来直接在硬件上运行的错觉。EPT由管理程序管理,与普通的页表类似,只是它把每个客户的物理地址翻译成主机的物理地址。
Intro for DangZero
每当程序申请内存的时候,都会被分配到唯一虚拟地址,当内存被释放之后,唯一的虚拟地址索引会被无效化,通过在内存映射表中将该地址设置为invalid;但是物理内存地址仍然可以被重复使用。
整体架构如下:
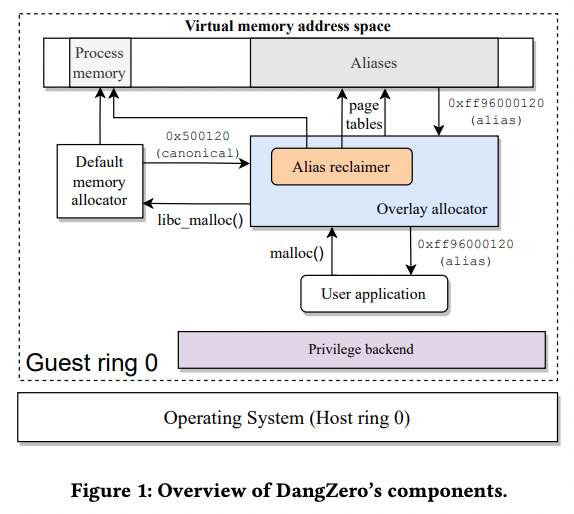
4-1
DangZero builds on the idea of aliasing [18], where each object has its own virtual alias, but multiple objects share the same underlying physical page. Figure 2 visualizes how the different pages relate to each other. We refer to the virtual page returned by the default memory allocator as the canonical page. These pages can contain multiple memory objects by design (up to 128 objects on a 4K page). The physical page backing the canonical page matches the objects. Then, for each individual object, there is a distinct alias page, with the in-page offset matching the canonical page. If the original allocation spans multiple pages, the resulting object will have the same number of corresponding alias pages.
4-2
With DangZero, we can directly modify the page tables from our overlay allocator instead, completely outside of the control of the operating system. DangZero takes over an unused area of the virtual address space, that is never touched by the kernel, and directly writes into the page table page entries corresponding to that area. To facilitate this access to (normally) restricted resources, our privilege backend provides safe access. The design of DangZero is agnostic to the exact mechanism used, but in general it must support direct read and write access to page tables and allow for TLB flushing, while at the same time ensuring safety and isolation to the rest of the system. Our primary backend uses a guest running Kernel Mode Linux (KML) for transforming Linux into a libOS;
RELATED WORK
Secure Allocator
通过“改良”内存分配的allocators可以在一定程度上实现缓解UAF问题;
早起的解决方案,旨在通过引入随机化内存分配的方式,提高攻击者利用的难度;
Cling 以及 TAT通过在分配器中引入
type-safe机制,但是存在利用相同类型的object控制悬空指针的问题;余下的方案大多数是利用GC机制来解决UAF的问题;但是可能会大大的降低性能;
利用虚拟化技术实现安全隔离
一些项目将虚拟化扩展用于安全域的隔离;本文主要受相关文章的启发,在unikernel-style模式下对应用程序执行特权指令;
REFERENCE
感谢G.O.S.S.I.P公众号推荐的优秀论文